So it was discovered that Twitter has been granted a patent which covers detection of mobile malware on websites to protect its user base. The patent was filed back in 2012, but well – as we know these things take time.
The method is something like the technology Google uses in Chrome to warn you if a webpage is malicious and it prompts you not to visit.
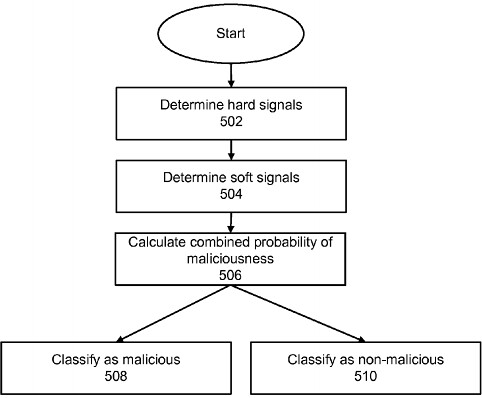
It utilises multiple signals to detect mobile malware and protect the user from being infected (by calculating the probably of the page being malicious).
Twitter has been granted a patent for detecting malware on mobile sites, according to a filing made public this month.
According to the patent, filed back in 2012, Twitter could protect users from malware by crawling websites with “an emulated mobile device to cause behaviors to occur which may be malicious.” After Twitter’s bot visits a given mobile site, the “behaviors … are stored [and] classified as hard or soft signals.”
From there, Twitter’s patent describes a method for assessing the “probability of the webpage being malicious,” after which it is “classified as malicious or non-malicious.” Finally, Twitter describes how visitors of the site, the site’s developer, and the “distributor of the webpage” (perhaps the user who tweeted the link) will be alerted if the site has been classified as malware.
It seems like social networks, search engines etc want to take more responsibility for protecting their users (like the malware warnings on search results within Google and the Chrome warning splash page.
They think it adds value to their networks, which it does in a way – and of course it makes the user experience more positive, which is always a benefit. And this is definitely a more pro-active response than just acting on user reports and spam flags.
Most interestingly, the patent mirrors a similar system already implemented by Google on Google.com and within Chrome. Google alerts users with a warning splash page [below] which attempts to block users from accessing the site.
Twitter’s interest in preventing the spread of malware highlights new responsibilities for the social network as it continues to grow. Implementing such a system does not directly affect Twitter in the way the company’s anti-spam efforts have. Instead, this initiative to crawl the mobile web for malware would be a preventative effort to keep Twitter’s name clean.
In VentureBeat’s own tests, Twitter did not flag any sites known by Google for distributing malware on iOS or desktop, suggesting that the tech behind the patent is not publicly in use. Reached for comment, Twitter offered a boilerplate response.
It seems the technology is not yet actually in use on the Twitter platform, as you can still spread malware laden URLs without warning.
Perhaps the technology is still in staging/testing phase – or perhaps they are starting to realise how long it takes to spider the web for malware. A very long time.
It’ll be interesting to see if they start using it soon.
Source: VentureBeat
