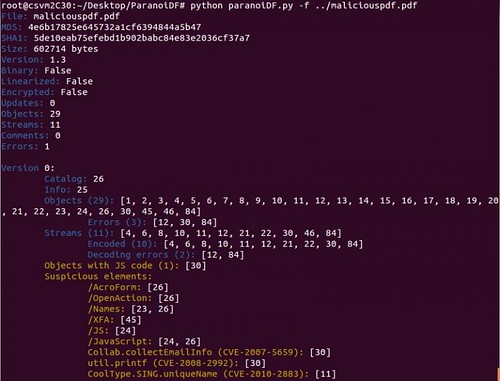
ParanoiDF is a PDF Analysis Suite based on PeePDF by Jose Miguel Esparza. The tools/features that have been added are – Password cracking, redaction recovery, DRM removal, malicious JavaScript extraction, and more.
We have posted about a few PDF related tools before, including the one this tool is based on:
– peepdf – Analyze & Modify PDF Files
– PDFResurrect v0.9 Released – PDF Analysis and Scrubbing Utility
– Origami – Parse, Analyze & Forge PDF Documents
Features
These are only the newly added features, not the original peepdf features which can be found here.
- crackpw – This executes Nacho Barrientos Arias’s PDFCrack tool by performing an OS call. The command allows the user to input a custom dictionary, perform a benchmark or continue from a saved state file. If no custom dictionary is input, this command will attempt to brute force a password using a modifiable charset text file in directory “ParanoiDF/pdfcrack”.
- decrypt – This uses an OS call to Jay Berkenbilt’s “QPDF” which decrypts the PDF document and outputs the decrypted file. This requires the user-password.
- encrypt – Encrypts an input PDF document with any password you specify. Uses 128-bit RC4 encryption.
- embedf – Create a blank PDF document with an embedded file. This is for research purposes to show how files can be embedded in PDFs. This command imports Didier Stevens Make-pdf-embedded.py script as a module.
- embedjs – Similiar to “embedf”, but embeds custom JavaScript file inside a new blank PDF document. If no custom JavaScript file is input, a default app.alert messagebox is embedded.
- extractJS – This attempts to extract any embedded JavaScript in a PDF document. It does this by importing Blake Hartstein’s Jsunpackn’s “pdf.py” JavaScript tool as a module, then executing it on the file.
- redact – Generate a list of words that will fit inside a redaction box in a PDF document. The words (with a custom sentence) can then be parsed in a grammar parser and a custom amount can be displayed depending on their score. This command requires a tutorial to use. Please read “redactTutorial.pdf” in directory “ParanoiDF/docs”.
- removeDRM – Remove DRM (editing, copying etc.) restrictions from PDF document and output to a new file. This does not need the owner-password and there is a possibility the document will lose some formatting. This command works by calling Kovid Goyal’s Calibre’s “ebook-convert” tool.
You can download ParanoiDF here:
Or read more here.
