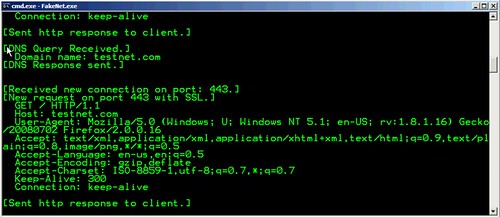
FakeNet is a Windows Network Simulation Tool that aids in the dynamic analysis of malicious software. The tool simulates a network so that malware interacting with a remote host continues to run allowing the analyst to observe the malware’s network activity from within a safe environment.
The goal of the project is to:
- Be easy to install and use; the tool runs on Windows and requires no 3rd party libraries
- Support the most common protocols used by malware
- Perform all activity on the local machine to avoid the need for a second virtual machine
- Provide python extensions for adding new or custom protocols
- Keep the malware running so that you can observe as much of its functionality as possible
- Have a flexible configuration, but no required configuration
The tool is in its infancy of development. The team started working on the tool in January 2012 and intend to maintain the tool and add new and useful features. If you find a bug or have a cool feature you think would improve the tool please do contact them.
Features
- Supports DNS, HTTP, and SSL
- HTTP server always serves a file and tries to serve a meaningful file; if the malware request a .jpg then a properly formatted .jpg is served, etc. The files being served are user configurable.
- Ability to redirect all traffic to the localhost, including traffic destined for a hard-coded IP address.
- Python extensions, including a sample extension that implements SMTP and SMTP over SSL.
- Built in ability to create a capture file (.pcap) for packets on localhost.
- Dummy listener that will listen for traffic on any port, auto-detect and decrypt SSL traffic and display the content to the console.
Right now the tool only supports WinXP Service Pack 3. The tool runs fine on Windows Vista/7 although certain features will be automatically disabled.
You can download FakeNet here:
Or read more here.
