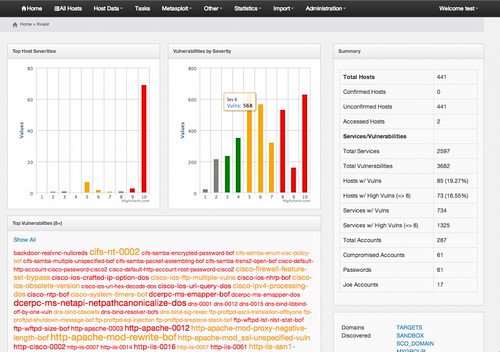
Penetration Testing Data Management can be a nightmware, because well you generate a LOT of data and some information when conducing a penetration test, especially using tools – they return lots of actual and potential vulnerabilitites to review. Port scanners can return thousands of ports for just a few hosts. How easy is it to share all this data with your co-workers?
Features
That’s what Kvasir is here to help you with. Here’s what you’ll need to get started:
- The latest version of web2py
- A database (PostgreSQL known to work)
- A network vulnerability scanner (Nexpose/Nmap supported)
- Additional python libraries
- Kvasir is a web2py application and can be installed for each customer or task.
Tools Supported
At current release, Kvasir directly supports the following tools:
- Rapid7 Nexpose Vulnerability Scanner
- Nmap Security Scanner
- Metasploit Pro (limited support for Express/Framework data)
- ShodanHQ
- ImmunitySec CANVAS
- THC-Hydra
- Foofus Medusa
- John The Ripper
This design keeps data separated and from you accidentally attacking or reviewing other customers.
This tool was developed primarily for the Cisco Systems Advanced Services Security Posture Assessment (SPA) team. While not every method used by the SPA team may directly relate we hope that this tool is something that can be molded and adapted to fit almost any working scenario.
Installation
Kvasir was primarily designed for use on short customer-focused engagements. A directory ‘application’ for each customer would be used allowing for much stronger data separation.
For example lets assume two customers, Foo Widgets and Bar Napkins.
Data for each customer is stored in /opt/data/$CUSTOMERNAME
Install Kvasir in each customer’s directory:
|
1 2 |
git clone https://github.com/KvasirSecurity/Kvasir /opt/data/foowidgets/kvasir git clone https://github.com/KvasirSecurity/Kvasir /opt/data/barnapkins/kvasir |
Now symbolically link Kvasir to the web2py application directory:
|
1 2 |
ln -s /opt/data/foowidgets/kvasir $WEB2PY_HOME/applications/foowdigets ln -s /opt/data/barnapkins/kvasir $WEB2PY_HOME/applications/barnapkins |
Create unique databases:
|
1 2 3 |
sudo su - postgres createdb -O pguser foowidgets createdb -O pguser barnapkins |
Copy the kvasir.yaml.sample to kvasir.yaml and change the defaults:
|
1 |
db->kvasir->uri |
Or read more here.

Dominick says
Sometimes when you get thousands of ports it can be confusing to everyone else but yourself. This tool you’re bringing to light seems to be a game changer! I hope this makes it easy to identify the more critical posts rather than having to siphon through thousands hoping there are a couple!