The BlindElephant Web Application Fingerprinter attempts to discover the version of a (known) web application by comparing static files at known locations against precomputed hashes for versions of those files in all all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable.
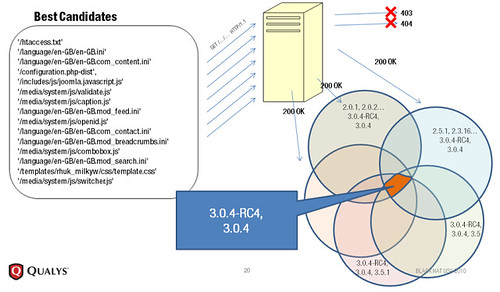
BlindElephant can be used directly as a tool on the command line, or as a library to provide fingerprinting functionality to another program.
Features
- Fast, low-resource approach (generally <6 seconds and < 400kb)
- Support for 15 commonly deployed web apps (and hundreds of versions), and very easy to add support for more
- Support for web app plugins (Drupal and WordPress currently, more with community input)
There are other similar projects such as:
– WAFP – Web Application Finger Printing Tool
– WhatWeb – Next Gen Web Scanner – Identify CMS (Content Management System)
– wig – WebApp Information Gatherer – Identify CMS
– Web-Sorrow v1.48 – Version Detection, CMS Identification & Enumeration
– Wappalyzer – Web Technology Identifier (Identify CMS, JavaScript etc.)
You can grab BlindElephant from the SVN repo here:
|
1 |
svn co https://blindelephant.svn.sourceforge.net/svnroot/blindelephant/trunk blindelephant |
Or read more here.
