‘Analytical Log Interface’ was built to sit on top of OSSEC (built on OSSEC 2.6) and requires 0 modifications to OSSEC or the database schema that ships with OSSEC. AnaLogi requires a Webserver sporting PHP and MySQL.
Written for inhouse analysis work, released under GPL to give something back – it’s intended to help you spot trends in graphs from hosts/levels/ruleID breakdowns and then let the user drill down to the specific alerts.
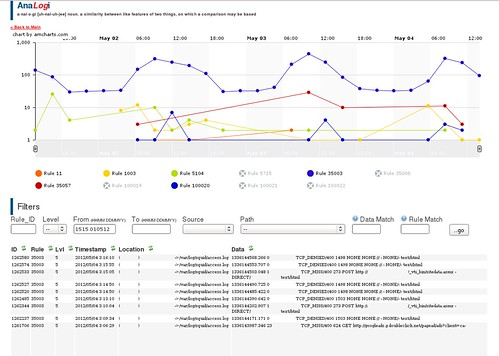
OSSEC is used for internal servers, therefore server names are treated as trusted and are not filtered for security within this project. For the same reason user input on the details page is not filtered… if you want to inject SQL, go ahead, you are the Sys Admin after all.
Log data IS treated as UNTRUSTED, and is validated before dumping to screen.
This was written and tested on a Virtual Machine, quad core, 4GB ram using a database with currently 1.2million alerts and 10 servers and performs fine.
If the interface gets slow over time you may want to consider your data retention period in the database and clean events out from time to time.
Download AnaLogi v1.1 here:
Or read more here.
