xSQL Scanner is a advanced SQL audit tool that allows users to find weak passwords and vulnerabilities on MS-SQL and MySQL database servers.
The objective of xSQLScanner is to assist the Security Analyst or Penetration Tester in auditing the security of MS-SQL and MySQL database servers.
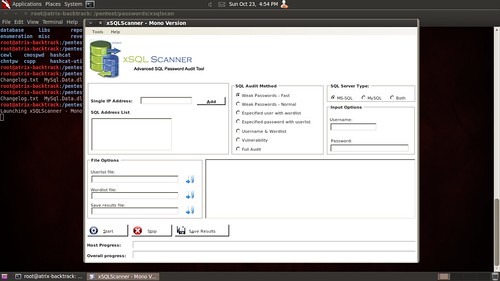
Features
- Test for weak password fast;
- Test for wear/user passwords;
- Wordlist option;
- Userlist option;
- Portscanner
- Range IP Address audit and more.
Windows – xsqlscanner-1.2.zip
Linux – xsqlscan-mono.tgz
Or read more here.

cypherinfo says
What is the way to decipher a password as you may see it in a mysql table from MD5?
Thank you.
Bogwitch says
You can’t decipher an MD5 hash. What you can do is generate hashes from known plaintext to see if they match the MD5. Whether that is generated from a dictionary, brute force or pre-computed rainbow tables is up to you.
for a good video that explains password hashing, go here http://www.youtube.com/watch?v=FYfMZx2hy_8
cypherinfo says
Thank you for your interest; great video! One thing only: what is the exact term used for the algorithm: “saw”, “aught”?
Thank you.
D3F says
4share was verry slow overhere. So i post a mirror on Docsbird.com
http://docsbird.com/?p=getfile&id=49da0bbc5d782dd140623fa735f9fd94c9411956
Mr H says
Thanks for posting this. DB security for some reason is consistently ignored in most organizations. Having an auditing tool to ensure the security of data warehouses is extremely important.
infodox says
Not entirely how much this differs from a sexed-up nmap/hydra combination, but it is still good to have a “clicky” tool – especially when doing a demo for an idiot CSO. I am not sure though… Does this have any serious performance benefits compared to hydra or ncrack?
Darknet says
Honestly not sure how well this would scale for large audits, I haven’t tested it extensively.
I’d be interested if anyone has any feedback though.