Vega vulnerability scanner is an open source web security tool to test the security of web applications. Vega can help you find and validate SQL Injections, Cross-Site Scripting (XSS), inadvertently disclosed sensitive information, and other vulnerabilities.
It is written in Java, GUI based, and runs on Linux, OS X, and Windows and includes an automated scanner for quick tests and an intercepting proxy for tactical inspection. Vega can be extended using a powerful API in the language of the web: Javascript.
Vega Vulnerability Scanner Features
Vega can help you find vulnerabilities such as: reflected cross-site scripting, stored cross-site scripting, blind SQL injection, remote file include, shell injection, and others. Vega also probes for TLS / SSL security settings and identifies opportunities for improving the security of your TLS servers.
- Automated Crawler and Vulnerability Scanner
- Consistent UI
- Website Crawler
- Intercepting Proxy
- SSL MITM
- Content Analysis
- Extensibility through a Powerful Javascript Module API
- Customizable alerts
- Database and Shared Data Model
Automated Scanner
Vega includes a website crawler powering its automated scanner. Vega can automatically log into websites when supplied with user credentials.
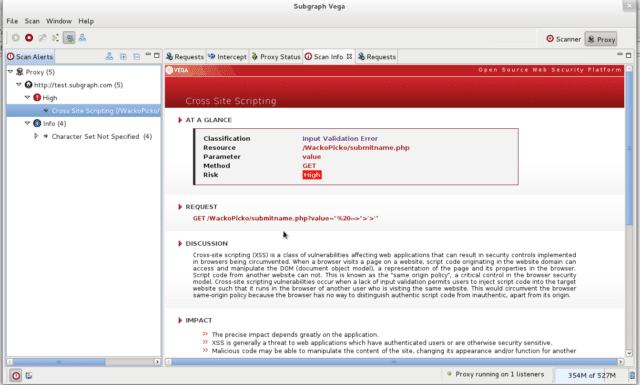
Intercepting Proxy
Vega can be used to observe and interact with communication between clients and servers, and will perform SSL interception for HTTP websites.
Proxy Scanner
The Vega proxy can also be configured to run attack modules while the user is browsing the target site through it. This allows for semi-automated, user-driven security testing to ensure maximum code coverage.
Vega Tool Modules
- Cross Site Scripting (XSS)
- SQL Injection
- Directory Traversal
- URL Injection
- Error Detection
- File Uploads
- Sensitive Data Discovery
There is some great documentation for getting started here or check out the intro to the Vega Proxy here.
You can download Vega here:
Windows – 32-bit/64-bit
Linux – 32-bit/64-bit
Mac OS X – 32-bit/64-bit
Or read more here.
