Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
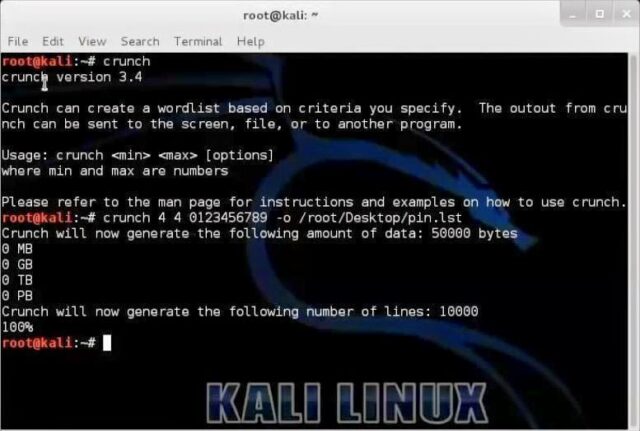
Some other options are:
- The Associative Word List Generator (AWLG) – Wordlists for Password Cracking
- CeWL – Custom Word List Generator Tool for Password Cracking
- RSMangler – Keyword Based Wordlist Generator For Bruteforcing
- CUPP – Common User Passwords Profiler – Automated Password Profiling Tool
Of course John the Ripper (JTR) has some built in options for creating permutations from Wordlists.
Crunch – Password Cracking Wordlist Generator Features
- Crunch generates wordlists in both combination and permutation ways
- It can breakup output by number of lines or file size
- Now has resume support
- Pattern now supports number and symbols
- Pattern now supports upper and lower case characters separately
- Adds a status report when generating multiple files
- now has unicode support
You can download Crunch wordlist generator here:
Or read more here.
