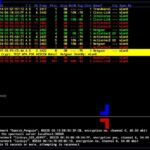
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. It will work with any wireless card which supports raw monitoring (rfmon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic. What is Kismet? Kismet differs from other wireless network detectors in working passively. Namely, without sending any loggable packets, it is […]
Archives for February 2008
January Commenter of the Month Competition Winner!
[ad] Competition time again! As you know we started the Darknet Commenter of the Month Competition on June 1st and it ran for the whole of June and July. We have just finished the eigth month of the competition in January and are now in the ninth, starting a few days ago on February 1st […]
FireCAT 1.3 Released – Firefox Catalog of Auditing Extensions
[ad] FireCAT is a Firefox Framework Map collection of the most useful security oriented extensions. Version 1.3 was pending the ExploitMe tools availability to the public. Changes for version 1.3 Category Information Gathering (Googling and Spidering) GSI Google Site indexer (GSI Creates Site Maps based on Google queries. Useful for both Penetration Testing and Search […]
German Police Creating Law Enforcement Trojan
After banning hacking tools it looks like the German police are looking into digital wiretapping and creating ‘whitehat’ trojans for monitoring the bad guys… Of course they define who the bad guys are, and according to law 202(c) it could be us.. This is very definitely questionable when it comes to ethics, it’s almost as […]