GoldenEye is a brute-force password cracker hacking program and here you can download goldeye.zip or goldeneye.zip – it was written for web-masters to test the web application security of their own sites. This is an oldskool file, a lot of people are still looking for this.
It should not be use by others to hack sites – this would be illegal! Under no circumstances should the author or any other persons involved in its development or distribution be held liable for the misuse of the program.
Once again these old files and tutorials are meant for the purpose of learning, test them in your own lab, see how they work, see what they do then try and write something similar yourself.
Using GoldenEye (GoldEye) Password Cracker
GoldenEye works with different types of wordlists:
|
1 |
"username:password", "username [TAB] password" or single lists |
GoldenEye executes its attempts simultaneously. The number of simultaneous attempts can be adjusted with the speed slider on the “access” tab. You can also adjust the speed limit. On the Options|Connections tab you’ll find a box to set the “top-speed”; select an apropiate value. Use lower values for slow internet connection!
If you get to much timed-out connections, lower the crack speed or increase the TTL (time to life). Timed-out connections will be automatically resumed if you check ‘Resume time-out connections automatically’ on the same tab.
Note: The program is tested with 70 simultaneous request. If you choose a higher value, do it on your own risk! If GoldenEye tells you something about buffer problems, lower the speed next time. I’ve encountered that other running programs may cause buffer problems.
GoldenEye logs the cracked sites. They are listed on the History|Access History tab. You can select and delete single entries or the whole list. Expired combinations will be automatically removed when you click the check for expired passwords button. Click on the ‘visit button’ or double click on the selected url to launch it in your browser.
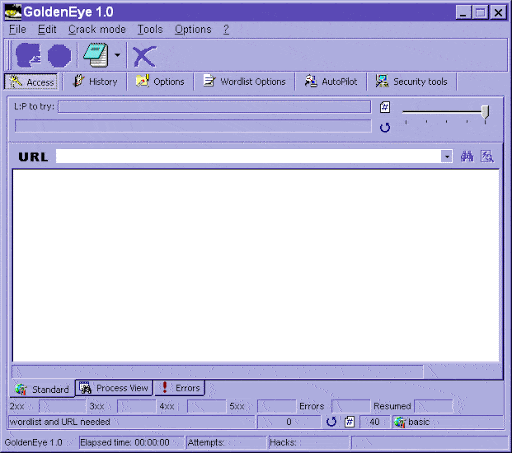
Access tab
The url box: if you don’t remember the members url you can
- search through the list
- or you type in a part off the url or a defined site name (see History|URL History) and click on the small button at the right end of the url-box.
Options|Advanced tab:
- Change proxy after x attempts: GoldenEye changes the proxy automatically after x attempts if this options is checked.You have to use several proxies to use this feature. Add proxies on the Options|connections tab.GoldenEye changes the proxy randomly or in the order which is given by the proxy-list.
- Server Response: the standard values are ‘200’ for ok and ‘401’ for access denied (unauthorized). If the server you’re attacking gives other reply numbers you can change them. Note: You can’t use 404 or 500!
- Cookie: If the attacked server needs a cookie, check this option and enter the cookie string.
- Referer: If the attacked server needs the url of the refering site, enter it here.
Wordlist tools tab
- Remove dupes: New: If you’re using single lists for userID and password GoldenEye removes the dupes simultaneous.
- General wordlist options:
- Define a mininum and maximum length for the userID and password (standard settings 1-32)
- Convert the list: All passes will be converted ‘on-the-fly’.
- Wordlist style: If you want to use single lists: check this option.
- Wordlist manipulations: this tab appears after you’ve loaded a list and checked the ‘Extend list’ on “General wordlist”
“Common manipulations” are predefined manipulations.
On the “Advanced” tab you can choose your own prefixes, suffixes, etc. If you miss something, tell me!
Security check
- Server security test: It tests the attacked server for other security holes.
- Proxy test: tests the proxy-speed. The values are in milliseconds.
Your anti-virus software may find a Win32.Gen.Trojan or similar in this file, that’s normal for most hacking software. Darknet in no way implies that this software is safe and free of malware, use at your own risk.
You can download GoldenEye 1.0 here.
To avoid any network issues the zip file is passworded, the password is darknet123.

.mario says
Hmmm, AntiVir says BDS/Delf.JM – what say you?
.mario says
ah sorry – didn’t finish reading. nevermind ;)
Marko_Catone says
It says I need a password for the encrypted file, (Goldeneye.rtf) How do I get one?
pzepf says
how do i install this exactly. it keeps giving me errors on it. can you specify it. I install it and then try to move it to the folder i have and it keeps telling me that it will not run.
Stephene says
how do u open it, i cant find it what buttons do u press
ollied says
Sure i will hack to learn via doi, just wanna get fulltext journal thats all, Oh…sciencedirect never mind!!
Jack of trades says
Can’t get it to work, when I try to run it nothing happens. Any help please?
web master says
every time i run goldeneye.exe it says that windows does not hav appropriate permission to open the file???see a problem?
god says
you have to be an idiot to download this its a trojan virus that will f up your pc
Cobra says
Very handy for my project on security systems…
yourname says
How do I install this in ubuntu? When I try to run through WINE it get a
application error.
Exception TICMPException in module GoldenEye.exe at 00092B92. Unable to get ping handle.
abdulla toghouj says
thats actually great to learn.
unknown283 says
where do you get a wordlist??????????
navin says
The same place where they shell out brains!!
anyways I’m in the mood to help so i’ll give U some pointers anyway
https://www.darknet.org.uk/2009/01/the-associative-word-list-generator-awlg-create-related-wordlists-for-password-cracking/
https://www.darknet.org.uk/2009/01/cewl-custom-word-list-generator-tool-for-password-cracking/
https://www.darknet.org.uk/2008/02/password-cracking-wordlists-and-tools-for-brute-forcing/
n00b!!
Bogwitch says
Wordlists available here