[ad] Ah the anti-trust battle continues, good to see someone with technical skills involved, I wonder how the case is coming along, I haven’t heard about it for a while. Again this is quite an old story. As an expert witness on digital crime, British computer consultant Neil Barrett has helped prosecutors in the United […]
Archives for September 2006
Impressive Open Source Intrusion Prevention – HLBR
It’s good to see work on open source tools in the countermeasure department aswell as the attack and penetration arena. It’s a shame since Snort and Nessus have gone semi-commercial. I hope more people invest their time in good IDS, Firewall and IPS systems, I love things like IPCop and hope to see more products […]
Using the capture command in a Cisco Systems PIX firewall.
This is an excellent article you might find useful covering the use of the capture command in Cisco PIX firewalls. A vital tool to use when troubleshooting computer networking problems and monitoring computer networks is a packet sniffer. That being said, one of the best methods to use when troubleshooting connection problems or monitoring suspicious […]
Moving Ahead in the War Against Botnets
[ad] This effort started quite a long time ago, I was just checking up to see how they were getting on, but there’s not much news of their progress. perating under the theory that if you kill the head, the body will follow, a group of high-profile security researchers is ramping up efforts to find […]
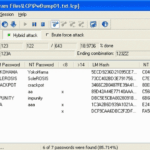
LCP Download – L0phtcrack LC5 Password Cracking Alternative
LCP Download below, LCP is tool focused on account password auditing and recovery, it’s a free alternative to L0phtcrack LC5. It was popular during the time of Windows NT/2000/XP/2003 and could import hashes from local and remote computers in SAM and PWDUMP file formats. What is LCP Windows Password Cracker? LCP is one of the […]