[ad]
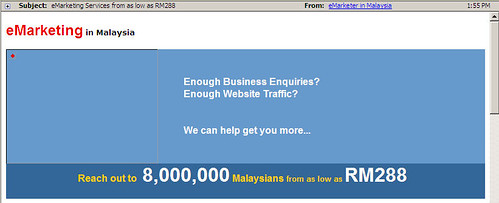
So a friend of mine received a spam, which is not unusual, but this one was a little different.
This guy is in Malaysia, and the spam he usually receives is from all over the place, mostly US-centric, but this one was targeting Malaysians, Malaysian spammer producing Malaysian spam, is it the first?
I asked for him to forward the mail to me so I could check it out, pretty standard spam.
I then noticed Thunderbird was blocking some external images so I checked the source of the e-mail (The from address was pretty anonymous “eMarketer in Malaysia” [email protected]).
The source indeed revealed the location of the imbedded images:
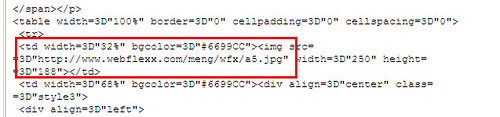
http://www.webflexx.com/meng/wfx/
Fee Structure
RM288 – 150,000 emails (one day trial)
RM388 – 500,000 emails
RM688 – 1,000,000 emails
RM1376 – 2,000,000 emails
RM2064 – 3,000,000 emails + 1,000,000 emails FREE + ad design FREE!!Reply with your contact number. Or call Ms Meng 012-205 1591 or Mr Lim 012- 302 3899
It seems this company webflexx does offer spamming services:
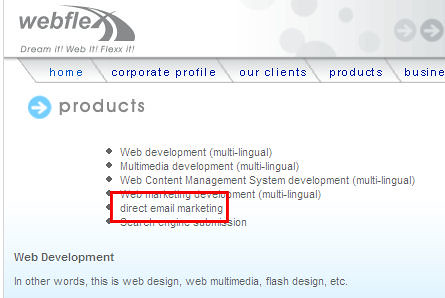
“direct email marketing” another term for spam right?
Notice the subdirectory of the spammer is /meng and the registrant of the webflexx domain is also an Ong Meng Foong, no coincidence right?
24-2 Plaza Damansara Jalan Medan Setia 2,
Bukit Damansara,
KL,50490
MY
Tel. +603.22835898
Going up one directory allowed me to browse the /meng directory, quite a nice collection of stuff.
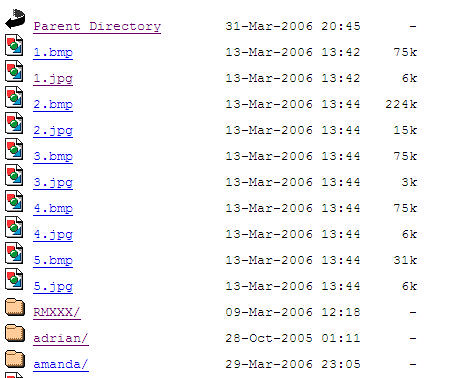
Browsing through the /meng directory I also found a screenshot of a personal ‘blog’ from Meng Foong.

Now whilst I couldn’t quite make out the text of the URL I could see the name “Meng’s Fickle Rambling Sessions”, which I of course Googled and found his blog, you can have a read here:
Seems like a nice Christian boy…from his blog I also found his Flickr Page (Inactive) and his old Xanga page.
From browsing the sub-directories it seems his clients are sexual based so far, sex toys, condoms and so on.


All his spam templates have this ‘disclaimer’ at the bottom:
Note: This email is meant for our potential clients. Should you have received it in error, please reply “unsubscribe” at the subject header. Thank you.
He or a friend named Amanda seems to be a student or ex-student of Help University college and a member of the Christian Fellowship there.
A quick Google Search on his site doesn’t yield much, just a couple more directories nothing interesting (/images and /multimedia).
I know people have to make a living, but spamming is not the way ok.
I hope no-one out there supports these spammers by paying them for these services, and no one of you uses any of these services advertised through spam.
There are plenty of pictures too in the http://www.webflexx.com/meng/ directory, check /tiomans and /kk to see :)
Have fun and remember don’t spam. If you really don’t know why spam is bad, read this.
Note: If you read this post by mistake, please e-mail Darknet with “unsubscribe” in the subject.

Fashionasia says
eh….good spywork!! clap clap, next time i need to do some spywork i know who to look for.
but….noneed to be so bad la put up his name and personal details all, kesian the fellow.
Dzof says
I agree, good investigative work.
Loong says
pwned! =)
evilfoo says
Sweet !!… This dude didn’t even disable directory listing for images on his site.
jarra says
excellent work.
he even apologised, hahaha
http://omengos.blogspot.com/2006/04/apologies-to-malaysians-at-large.html
but still, what he did makes him an *&%#$ !!!
Darknet says
Fashionasia: Well just shows what can be exposed if you aren’t careful..
evilfoo: He didn’t disable directory listing at all…he’s deleted the directory now though.
jarra: Seems like he’s closed his blog now.
Andy says
it’s actually a dudette m- wonder how much flak they got from their personal info being online though.
Christian J. Koch says
seems his blog and the webflexx site is now offline!! lol
great work!
WTF! says
WTF!!! Whats the point?!
Danny Foo says
I think that’s one of it exposed. But there are others who do the same and the worst of the lot are the ones selling the information of emails to people. sigh..
Ken Woo says
Webflexx life again!. He try to cheat Google bot to SEO his site with Keyword “Emarketing Malaysia” and “E-marketing Malaysia”. This is the screen shot.
He Try to spam high keyword density to SEO his website. He really good in SPAM SPAM SPAM!!!!
Ken Woo says
Please goto this image URL : http://static.flickr.com/104/310052679_665c84670a.jpg?v=0 to view here spam skill
Webflexx says
Hi
I am the webflexx.com owner and I was the one exposed by Darknet. Yes, at one stage I was spamming but all that has stopped already by now. I did apologise for what I did, and I have already stopped.
I did not steal passwords nor pin numbers, and neither did I cheat anyone of their hard earned money and their innocence. I have never done any of those things. If I did, please bring it up and I’ll try to re-do where I have gone wrong. I was experimenting with a lot of things in the process to learn.
The Google Bot was not a cheat, I was just experimenting with the codes. I know people enjoy all these juicy news when one is being “exposed” like this. If Google Bot can capture the codes and list us, then it is a point to consider. I was reading all those emarketing articles and was just experimenting with it. Why wan to make a big issue of a learning process here?
Most of my clients are not sexual-based. INeedHouse is indeed one of the biggest (and perhaps the ONLY) adult store in Malaysia. And being in Malaysia, they are actually promoting safe sex. Perhaps adults activities are rampant everywhere but not in Malaysia. This is a Muslim country. If you do not believe me, simply be in touch with them. Just google INeedHouse and be in touch so that they can tell you the truth too.
It has almost been one year now since Darknet exposed me. And since then, everything has changed. I no longer conduct any spamming business. Not at all. I have stopped all that when I was first ‘exposed’. And I do not sell any email addresses to anyone.
We do proper business now, and we do it the right way. I know I have offended spam-victims, but all those have stopped since.
I do not run from making mistakes, so please hope to get your good understanding on all these things. I am not a cheater.
If you would like to call me on my mobile, simply call +60-12-205 1591 and let me apologise to you personally. You can also email me [email protected] and let me apologise.
If you are still unhappy, just contact me. No point going around and studying what is up and what is down and what I have done in the past. All those remain in the past.
If I can recover from what Darknet did in exposing me like this, why can’t the rest of the world follow suit?
Once again, please accept my apologies and I am truly sorry.
Webflexx says
To Ken Woo,
You’re definitely either a Malaysian or a Singaporean. Please be in touch with me. Please let me know if I have offended you.
You do not have to be too worked out on the keywords spamming in the index page. It was an experiment. Even if I did take those words away from the index page, there are other criterias that Google look into for SEOing a website, definitely not on the density of the keyword alone. If that is the case, then it would be an unfair way for Google to rank each pages, as all a website owner need to do is to repeat each keywords as often as possible.
Let me make my mistakes and let me learn. Just do not get too worked out over this. Everyone is trying their level best to get to the top 10 of Google.com, so let me learn how to get it done.
Thanks for your understanding Mr. Ken Woo. If you are still not happy, please be in touch with me.
To Mr Danny Foo,
I have also been reading your website and I have learned from you for a few months now. Hope to exchange opinion with you one day. I am not a cheater, a liar, and neither am I a stealer.
To the world, apologies once again.
Spikyles says
I found this article interesting and decided to test out the process with some of the spam I received. I found almost the exact situation for my spammer, the files, etc… anyone have any suggestions on what to do with the info? Pretty cool though.
Darknet says
Webflexx: Your website services still state you do direct email marketing, so you are still a spammer.
Spikyles: Report them to the upstream ISP the mail was sent from and the web host for the domain the spam image/site is hosted on that’s about the best you can do.
Webflexx says
Dear Darknet
Thanks for bringing this up. I have already taken down that one line. Trust me, we don’t spam anymore. Apologies once again for the misconception given.
I mean, I have already deleted the line that says we still offer direct email marketing.
Webflexx.