[ad]
Interesting to see which RSS aggregators and readers Digg users are using.
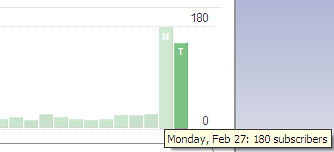
As you can see after being ‘digged’ on Monday February 27th, the RSS subscriber base spiked from about 21 up to 182 at the highest point, after a day it receded back to around 150, and now it’s about 130.
The biggest Agent in the graph by a large margin is Google Desktop.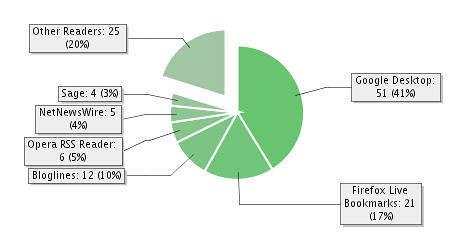
Some of the figures are not so accurage as services like Kinjo don’t give the number of subscribers.
Firefox Livebookmarks is also high, which I was expecting.
3rd place goes to Bloglines, probably the most popular web-based blog/RSS aggregator.
The RSS subscription percentage is quite high aswell, as around 20,000 people came on that day, and around 160 subscribed.
The above pictures were taken from the shiny new updated Feedburner control panel.
