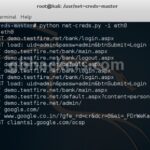
net-creds is a Python-based tool for sniffing plaintext passwords and hashes from a network interface or PCAP file – it doesn’t rely on port numbers for service identification and can concatenate fragmented packets. Features of net-creds for Sniffing Passwords It can sniff the following directly from a network interface or from a PCAP file: URLs […]
Python
Mr.SIP – SIP Attack And Audit Tool
Mr.SIP was developed in Python as a SIP Attack and audit tool which can emulate SIP-based attacks. Originally it was developed to be used in academic work to help developing novel SIP-based DDoS attacks and defence approaches and then as an idea to convert it to a fully functional SIP-based penetration testing tool, it has […]
RDPY – RDP Security Tool For Hacking Remote Desktop Protocol
RDPY is an RDP Security Tool in Twisted Python with RDP Man in the Middle proxy support which can record sessions and Honeypot functionality. RDPY is a pure Python implementation of the Microsoft RDP (Remote Desktop Protocol) protocol (client and server side). RDPY is built over the event driven network engine Twisted. RDPY support standard […]
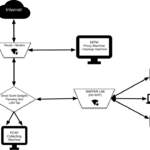
SNIFFlab – Create Your Own MITM Test Environment
SNIFFlab is a set of scripts in Python that enable you to create your own MITM test environment for packet sniffing through a WiFi access point. Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected to a “Man-in-the-middle” attack, whereby they can […]
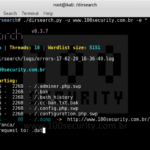
dirsearch – Website Directory Scanner For Files & Structure
dirsearch is a Python-based command-line website directory scanner designed to brute force site structure including directories and files in websites. dirsearch Website Directory Scanner Features dirsearch supports the following: Multithreaded Keep alive connections Support for multiple extensions (-e|–extensions asp,php) Reporting (plain text, JSON) Heuristically detects invalid web pages Recursive brute forcing HTTP proxy support User […]