[ad] psad is a collection of three lightweight system daemons (two main daemons and one helper daemon) that run on Linux machines and analyze iptables log messages to detect port scans and other suspicious traffic. A typical deployment is to run psad on the iptables firewall where it has the fastest access to log data. […]
intrusion-detection
PHPIDS – Security Layer & Intrusion Detection for PHP Based Web Applications
[ad] Another protection for those building website and web applications, as it’s the the most common attack vector nowadays I think it’s important to be extra safe on this front. PHPIDS (PHP-Intrusion Detection System) is a simple to use, well structured, fast and state-of-the-art security layer for your PHP based web application. The IDS neither […]
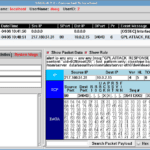
Sguil – Intuitive GUI for Network Security Monitoring with Snort
Sguil (pronounced sgweel) is probably best described as an aggregation system for network security monitoring tools. It ties your IDS alerts into a database of TCP/IP sessions, full content packet logs and other information. When you’ve identified an alert that needs more investigation, the sguil client provides you with seamless access to the data you […]
Agnitum Outpost Firewall PRO Review
[ad] Agnitum Outpost Firewall Pro is a software based firewall I respect a lot, and used to actually use…It used to be fairly light weight, secure and had some good features the other firewalls at the time didn’t have (system file integrity checking and so on). But nowadays with NAT routers, the need for desktop […]
Hackers Target Home Users for Cash
[ad] Hackers are switching targets now, companies are getting too hard to break into due to the availability of decently configured perimeter kit like firewalls and IDS. Plus the information they do get if they manage to break in is often worthless commercially and really not worth the effort. So instead, they target the end […]