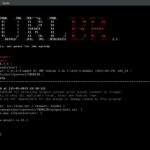
INURLBR is a PHP based advanced search engine tool for security professionals, it supports 24 search engines and 6 deep web or special options. Very useful for the information gathering phase of a penetration test or vulnerability assessment. This tool functions in many ways enabling you to harness the power of what’s already indexed by […]
information gathering
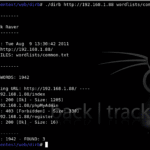
DIRB – Domain Brute-forcing Tool
DIRB is a Web Content Scanner AKA a domain brute-forcing tool. It looks for existing (and/or hidden) Web Objects, it works by launching a dictionary based attack against a web server and analysing the responses. What is DIRB? DIRB comes with a set of preconfigured attack word-lists for easy usage but you can use your […]
LNHG – Massive Web Fingerprinter (mwebfp)
The LowNoiseHG (LNHG) Massive Web Fingerprinter was conceived in July 2013 after realizing the usefulness of webserver screenshots to pentesters, during an engagement with large external or internal IP address ranges, as a quick means of identification of critical assets, easily-exploitable services, forgotten/outdated servers and basic network architecture knowledge of the target. The basic operation […]
SpiderFoot – Open Source Intelligence Automation Tool (OSINT)
SpiderFoot is an open source intelligence automation tool. Its goal is to automate the process of gathering intelligence about a given target, which may be an IP address, domain name, hostname or network subnet. SpiderFoot can be used offensively, i.e. as part of a black-box penetration test to gather information about the target or defensively […]
Scumblr by Netflix – Automatically Scan For Leaks
Scumblr is a search automation web application that helps you to automatically scan for leaks by performing periodic searches and storing / taking actions on the identified results. Scumblr uses the Workflowable gem to allow setting up flexible workflows for different types of results. How do I use Scumblr? Scumblr is a web application based […]