So Android Malware has always been quite a problem, especially with it being so easy to install random .apk files and the proliferation of 3rd party app stores. Also so many people with rooted phones and the fact that software installed can root your phone and take complete control. The current worry is the Hummer […]
Malware
Cuckoo Sandbox – Automated Malware Analysis System
Cuckoo Sandbox is Open Source software for automating analysis of suspicious files. To do so it makes use of custom components that monitor the behaviour of the malicious processes while running in an isolated environment. In other words, you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide […]
movfuscator – Compile Into ONLY mov Instructions
The M/o/Vfuscator (short ‘o’, sounds like “mobfuscator”) helps programs compile into only mov instructions, and nothing else – no cheating. Arithmetic, comparisons, jumps, function calls, and everything else a program needs are all performed through mov operations; there is no self-modifying code, no transport-triggered calculation, and no other form of non-mov cheating. The compiler currently […]
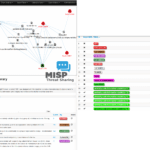
MISP – Malware Information Sharing Platform
MISP, Malware Information Sharing Platform and Threat Sharing, is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threat about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reverser to support their day-to-day operations to share […]
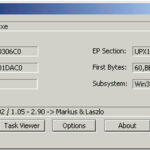
PEiD Download – Detect PE Packers, Cryptors & Compilers
PEiD is an intuitive application that relies on its user-friendly interface to detect PE packers, cryptors and compilers found in executable files – its detection rate is higher than that of other similar tools since the app packs more than 600 different signatures in PE files. What is PEiD? PEiD comes with three different scanning […]