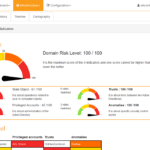
PingCastle is a Active Directory Security Assessment Tool designed to quickly assess the Active Directory security level with a methodology based on a risk assessment and maturity framework. It does not aim at a perfect evaluation but rather as an efficiency compromise. The risk level regarding Active Directory security has changed. Several vulnerabilities have been […]
Security Software
Astra – API Automated Security Testing For REST
Astra is a Python-based tool for API Automated Security Testing, REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs. Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra […]
AIEngine – AI-driven Network Intrusion Detection System
AIEngine is a next-generation interactive/programmable Python/Ruby/Java/Lua and Go AI-driven Network Intrusion Detection System engine with capabilities of learning without any human intervention, DNS domain classification, Spam detection, network collector, network forensics and many others. AIEngine also helps network/security professionals to identify traffic and develop signatures for use them on NIDS, Firewalls, Traffic classifiers and so […]
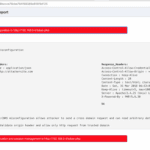
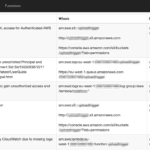
LambdaGuard – AWS Lambda Serverless Security Scanner
LambdaGuard is a tool which allows you to visualise and audit the security of your serverless assets, an open-source AWS Lambda Serverless Security Scanner. AWS Lambda is an event-driven, serverless computing platform provided by Amazon Web Services. It is a computing service that runs code in response to events and automatically manages the computing resources […]
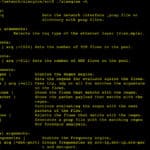
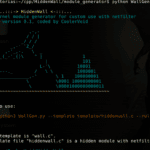
HiddenWall – Create Hidden Kernel Modules
HiddenWall is a Linux kernel module generator used to create hidden kernel modules to protect your server from attackers. It supports custom rules with netfilter (block ports, hidden mode, rootkit functions etc). The motivation is basically another layer of protection, much like a hidden firewall – setting securelevel to 2 on BSD would have a […]