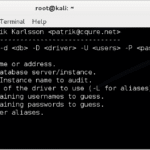
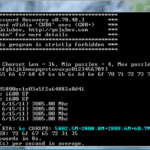
DBPwAudit is a Java database password auditing tool that allows you to perform online audits of password quality for several database engines. The application design allows for easy adding of additional database drivers by simply copying new JDBC drivers to the jdbc directory. Configuration is performed in two files, the aliases.conf file is used to […]
Password Cracking Tools
Password cracking and the associated password cracker tools are often the area of information security and hacking that people get most excited about, oh wow I can hack email passwords? We get emails pretty much every day asking how to crack someone's Facebook password, or retrieve website credentials etc.

What is Password Cracking?
As commonly defined:
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (brute-force attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password.
The purpose of password cracking might be to help a user recover a forgotten password (installing an entirely new password is less of a security risk, but it involves System Administration privileges), to gain unauthorized access to a system, or as a preventive measure by system administrators to check for easily crackable passwords. On a file-by-file basis, password cracking is utilized to gain access to digital evidence for which a judge has allowed access but the particular file's access is restricted.
From Wikipedia.
The Best Password Cracker Software
We have covered many of the most famous, some great examples are:
- Brutus Password Cracker – Download brutus-aet2.zip AET2
- THC-Hydra – The Fast and Flexible Network Login Hacking Tool
- Download pwdump 1.4.2 and fgdump 1.3.4 – Windows Password Dumping
- Cain & Abel – Download the Super Fast and Flexible Password Cracker with Network Sniffing
- JTR (Password Cracking) – John the Ripper 1.7 Released – FINALLY
- Ophcrack 2.2 Password Cracker Released
- hashcat – Multi-Threaded Password Hash Cracking Tool
- Medusa 2.0 Released – Parallel Network Login Brute Forcing Tool
And we have also published some related resources such as:
- Password Cracking Wordlists and Tools for Brute Forcing
- Password Cracking with Rainbowcrack and Rainbow Tables
IGHASHGPU – GPU Based Hash Cracking – SHA1, MD5 & MD4
IGHASHGPU is an efficient and comprehensive command line GPU based hash cracking program that enables you to retrieve SHA1, MD5 and MD4 hashes by utilising ATI and nVidia GPUs. It even works with salted hashes making it useful for MS-SQL, Oracle 11g, NTLM passwords and others than use salts. IGHASHGPU is meant to function with […]
SamParser – Parse SAM Registry Hives With Python
SamParser is a Python script used to parse SAM registry hives for both users and groups, it’s only dependency is python-registry. This would be a great little script to write into another toolset or larger attack pattern, especially if you’re already using a Python kit or framework. Dependencies
|
1 |
pip install python-registry |
Usage
|
1 |
python samparse.py <hive> |
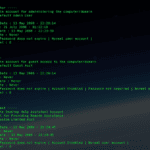
Sample Output
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
----- Administrator ----- Comment : Built-in account for administering the computer/domain Account Type : Default Admin User RID : 500 Account Created Date : 13 May 2008 - 22:20:14 Last Login Date : 21 July 2008 - 01:22:18 Password Reset Date : 13 May 2008 - 22:23:39 Password Fail Date : Never Account Flags : Password does not expire | Normal user account | Failed Login Count : 0 Login Count : 24 ----- Guest ----- Comment : Built-in account for guest access to the computer/domain Account Type : Default Guest Acct RID : 501 Account Created Date : 13 May 2008 - 22:20:14 Last Login Date : Never Password Reset Date : Never Password Fail Date : Never Account Flags : Password does not expire | Account Disabled | Password not required | Normal user account | Failed Login Count : 0 Login Count : 0 ----- Administrators ----- Group Description : Administrators have complete and unrestricted access to the computer/domain Last Write : 2008-05-14 05:35:35.281248 User Count : 7 Memebers : S-1-5-21-484763869-796845957-839522115-500 S-1-5-21-484763869-796845957-839522115-1003 S-1-5-21-484763869-796845957-839522115-1004 S-1-5-21-484763869-796845957-839522115-1005 S-1-5-21-484763869-796845957-839522115-1006 S-1-5-21-484763869-796845957-839522115-1007 S-1-5-21-484763869-796845957-839522115-1008 ----- Users ----- Group Description : Users are prevented from making accidental or intentional system-wide changes. Thus, Users can run certified applications, but not most legacy applications Last Write : 2008-05-14 05:35:35.265625 User Count : 8 Memebers : S-1-5-4 S-1-5-11 S-1-5-21-484763869-796845957-839522115-1003 S-1-5-21-484763869-796845957-839522115-1004 S-1-5-21-484763869-796845957-839522115-1005 S-1-5-21-484763869-796845957-839522115-1006 S-1-5-21-484763869-796845957-839522115-1007 S-1-5-21-484763869-796845957-839522115-1008 |
You […]
RWMC – Retrieve Windows Credentials With PowerShell
RWMC is a Windows PowerShell script written as a proof of concept to Retrieve Windows Credentials using only PowerShell and CDB command-line options (Windows Debuggers). It allows to retrieve credentials from Windows 2003 to 2012 and Windows 10 (It was tested on 2003, 2008r2, 2012, 2012r2 and Windows 7 – 32 and 64 bits, Windows […]
123456 Still The Most Common Password For 2015
So sadly, but also unsurprisingly ‘123456’ is still the most common password for 2015 (based on leaked password lists) the same as it was in years before, e.g. The 25 Worst Passwords Of 2013 – “password” Is Not #1. Way back in 2006, it clocked in at number 5 in a rather UK centric look […]