A Kiev power outage last weekend in Ukraine has been linked to a cyber attack, which is worryingly similar to an attack that happened around the same time last year. Sub-stations and transmission stations have always been a weak point for nation-state attacks as EVERYTHING relies on them now. Plus with smart grids and remotely […]
Hardware Hacking
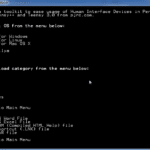
Kautilya – Human Interface Device Hacking Toolkit
Kautilya is a human interface device hacking toolkit which provides various payloads for HIDs which may help with breaking into a computer during penetration tests. The Windows payloads and modules are written mostly in powershell (in combination with native commands) and are tested on Windows 7 and Windows 8. In principal Kautilya should work with […]
Tesla Hack – Remote Access Whilst Parked or Driving
The big buzz on my Twitter this week was about the Tesla Hack carried out by a Chinese crew called Keen Security Lab. It’s no big surprise even though Tesla is known for being fairly security concious and proactive about it. With it being a connected car, that’s pretty important that any remote control capabilities […]
In 2016 Your Wireless Keyboard Security Still SUCKS – KeySniffer
So you’d probably imagine that Wireless Keyboard Security is a 1998 problem and you shouldn’t even have to worry about that any more. And you’d be wrong – two-thirds of wireless keyboards, from MAJOR manufacturers are not even vaguely secure. It turns out, in 2016 when cryptography is mainstream, open-source and fairly easy to implement […]
Intel Hidden Management Engine – x86 Security Risk?
So it seems the latest generation of Intel x86 CPUs have implemented a Intel hidden management engine that cannot be audited or examined. We can also assume at some point it will be compromised and security researchers are labelling this as a Ring -3 level vulnerability. This isn’t a new issue though, people have been […]