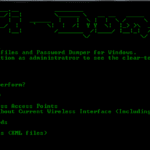
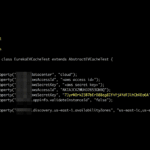
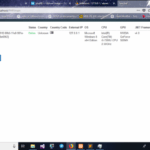
WiFi-Dumper is an open-source Python-based tool to dump WiFi profiles and cleartext passwords of the connected access points on a Windows machine. This tool will help you in a Wifi penetration testing and could also be useful when performing red team assessments or internal infrastructure engagements. Each option in the tool generates the “.txt” file […]
Hacking Tools
Hacking Tools are pieces of software or programs created to help you with hacking or that users can utilise for hacking purposes.
Examples include Wep0ff – Wifi Cracking Tool, Brutus Password Cracker, wwwhack Web Hacking, THC-Hydra Network Login Hacking and pwdump/fgdump Windows Password Dumping Tools.

You can find the latest and best hacking tools below and more on Wikipedia.
Script Kiddie Hacking Tools
There are various tools that are classified as too easy to use, or too automated and these fall into the category of Script Kiddie Tools. These are people who just follow instructions from a manual or tutorial without really understanding the technology or process happening.
Examples of these tools would mainly be password cracking tools like Cain and Abel Password Cracker, Brutus Password Cracker and John the Ripper for Password Cracking.
truffleHog – Search Git for High Entropy Strings with Commit History
truffleHog is a Python-based tool to search Git for high entropy strings, digging deep into commit history and branches. This is effective at finding secrets accidentally committed. truffleHog previously functioned by running entropy checks on git diffs. This functionality still exists, but high signal regex checks have been added, and the ability to surpress entropy […]
UBoat – Proof Of Concept PoC HTTP Botnet Project
UBoat is a PoC HTTP Botnet designed to replicate a full weaponised commercial botnet like the famous large scale infectors Festi, Grum, Zeus and SpyEye. Reviews of popular botnets have shown HTTP-based botnets have a set of attributes that make it difficult for them to be detected. On the other hand, the number of studies […]
Stardox – Github Stargazers Information Gathering Tool
Stardox is a Python-based GitHub stargazers information gathering tool, it scrapes Github for information and displays them in a list tree view. It can be used for collecting information about your or someone else’s repository stargazers details. GitHub allows visitors to star a repo to bookmark it for later perusal. Stars represent a casual interest […]
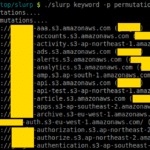
Slurp – Amazon AWS S3 Bucket Enumerator
Slurp is a blackbox/whitebox S3 bucket enumerator written in Go that can use a permutations list to scan from an external perspective or an AWS API to scan internally. There are two modes that this tool operates at; blackbox and whitebox mode. Whitebox mode (or internal) is significantly faster than blackbox (external) mode. Blackbox (external) […]