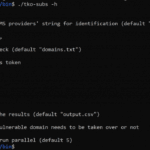
tko-subs is a tool that helps you to detect & takeover subdomains with dead DNS records, this could be dangling CNAMEs point to hosting services or to nothing at all or NS records that are mistyped. What does tko-subs – Detect & Takeover Subdomains With Dead DNS Records Do? This tool allows you: To check […]
Hacking Tools
Hacking Tools are pieces of software or programs created to help you with hacking or that users can utilise for hacking purposes.
Examples include Wep0ff – Wifi Cracking Tool, Brutus Password Cracker, wwwhack Web Hacking, THC-Hydra Network Login Hacking and pwdump/fgdump Windows Password Dumping Tools.

You can find the latest and best hacking tools below and more on Wikipedia.
Script Kiddie Hacking Tools
There are various tools that are classified as too easy to use, or too automated and these fall into the category of Script Kiddie Tools. These are people who just follow instructions from a manual or tutorial without really understanding the technology or process happening.
Examples of these tools would mainly be password cracking tools like Cain and Abel Password Cracker, Brutus Password Cracker and John the Ripper for Password Cracking.
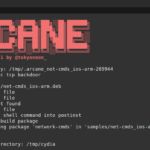
Arcane – Tool To Backdoor iOS Packages (iPhone ARM)
Arcane is a simple script tool to backdoor iOS packages (iPhone ARM) and create the necessary resources for APT repositories. It was created to help illustrate why Cydia repositories can be dangerous and what post-exploitation attacks are possible from a compromised iOS device. How Arcane Tool To Backdoor iOS Package Works It’s possible to supply […]
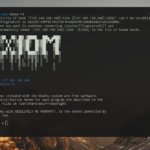
Axiom – Pen-Testing Server For Collecting Bug Bounties
Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty, basically a pen-testing server out of the box with 1-line. With Axiom, you just need to run a single command to get setup, and then you can use the Axiom toolkit scripts to spin up and down your […]
Quasar RAT – Windows Remote Administration Tool
Quasar is a fast and light-weight Windows remote administration tool coded in C#. The usage ranges from user support through day-to-day administrative work to employee monitoring. It aims to provide high stability and an easy-to-use user interface and is a free, open source tool. Features of Quasar RAT Windows Remote Administration Tool The main features […]
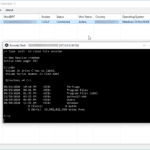
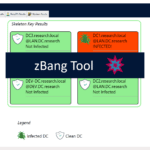
zBang – Privileged Account Threat Detection Tool
zBang is a risk assessment tool for Privileged Account Threat Detection on a scanned network, organizations and red teamers can utilize zBang to identify potential attack vectors and improve the security posture of the network. The results can be analyzed with the graphic interface or by reviewing the raw output files. The tool is built […]