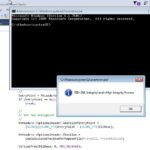
UACme is a compiled, C-based tool which contains a number of methods to defeat Windows User Account Control commonly known as UAC. It abuses the built-in Windows AutoElevate backdoor and contains 41 methods. The tool requires an Admin account with the Windows UAC set to default settings. Usage Run executable from command line: akagi32 [Key] […]
Exploits/Vulnerabilities
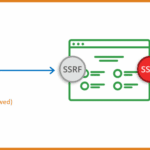
What You Need To Know About Server Side Request Forgery (SSRF)
SSRF or Server Side Request Forgery is an attack vector that has been around for a long time, but do you actually know what it is? Server Side Request Forgery (SSRF) refers to an attack where in an attacker is able to send a crafted request from a vulnerable web application. SSRF is usually used […]
US Voting Machines Hacked At DEF CON – Every One
US Voting Machines Hacked, some in minutes at this year’s DEF CON “Voting Village” – not something you want to hear really. Especially with the results of recent elections that the World is currently dealing with the consequences from. Of course with physical access, most machines can be dominated in some way or another – […]
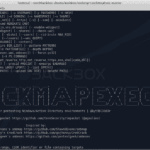
CrackMapExec – Active Directory Post-Exploitation Tool
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve its functionality and allowing it to evade most endpoint protection/IDS/IPS solutions. CME makes heavy use of […]
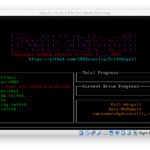
EvilAbigail – Automated Evil Maid Attack For Linux
EvilAbigail is a Python-based tool that allows you run an automated Evil Maid attack on Linux systems, this is the Initrd encrypted root fs attack. An Evil Maid attack is a type of attack that targets a computer device that has been shut down and left unattended. An Evil Maid attack is characterized by the […]