The debate surrounding encryption backdoors has been raging on for years with governments (that typically don’t really understand the things they are pushing for) requesting all software have government ‘secured’ backdoor keys. This is now getting more serious in Europe with the EC actually forcing the issue (in a passive aggressive kind of way for […]
Cryptography
HashPump – Exploit Hash Length Extension Attack
HashPump is a C++ based command line tool to exploit the Hash Length Extension Attack with various hash types supported, including MD4, MD5, SHA1, SHA256, and SHA512. There’s a good write-up of how to use this in practical terms here: Plaid CTF 2014: mtpox Usage
|
1 2 3 4 5 6 7 8 9 10 11 |
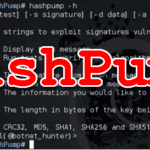
$ hashpump -h HashPump [-h help] [-t test] [-s signature] [-d data] [-a additional] [-k keylength] HashPump generates strings to exploit signatures vulnerable to the Hash Length Extension Attack. -h --help Display this message. -t --test Run tests to verify each algorithm is operating properly. -s --signature The signature from known message. -d --data The data from the known message. -a --additional The information you would like to add to the known message. -k --keylength The length in bytes of the key being used to sign the original message with. Version 1.2.0 with CRC32, MD5, SHA1, SHA256 and SHA512 support. <Developed by bwall(@botnet_hunter)> |
You can download HashPump here:
|
1 2 3 4 5 |
$ git clone https://github.com/bwall/HashPump.git $ apt-get install g++ libssl-dev $ cd HashPump $ make $ make install |
Or read more […]
ONIOFF – Onion URL Inspector
ONIOFF is basically an Onion URL inspector, it’s a simple tool – written in pure python – for inspecting Deep Web URLs (or onions). It takes specified onion links and returns their current status along with the site’s title. It’s compatible with Python 2.6 & 2.7. Usage
|
1 |
Usage: python onioff.py {onion} [options] |
To view all available options run:
|
1 |
$ python onioff.py -h |
[…]
hashID – Identify Different Types of Hashes
hashID is a tool to help you identify different types of hashes used to encrypt data, especially passwords. It’s written in Python 3 and supports the identification of over 220 unique hash types using regular expressions. hashID is able to identify a single hash, parse a file or read multiple files in a directory and […]
China To Outlaw All Unapproved Darknet VPN Services
So the latest news from behind the Great Firewall of China is that they plan to crack down on all unapproved Darknet VPN services. This means all VPN providers, cloud service providers and ISPs will have to seek an annually renewed licence to operate a VPN Service. Really, not very surprising coming out of China […]