A lot of people and companies get complacent and don’t believe the hackers are winning, but trust me they are. So we have to ask, why are hackers winning the security game? What’s putting them ahead of the security teams and CISOs inside organizations. It’s an old story anyway, the Hackers always win in some […]
Countermeasures
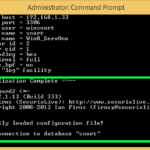
Barnyard2 – Dedicated Spooler for Snort Output
Barnyard2 is an open source dedicated spooler for Snort output as unified2 binary output files. Its primary use is allowing Snort to write to disk in an efficient manner and leaving the task of parsing binary data into various formats to a separate process that will not cause Snort to miss network traffic. How it […]
Wycheproof – Test Crypto Libraries Against Known Attacks
Project Wycheproof is a tool to test crypto libraries against known attacks. It is developed and maintained by members of Google Security Team, but it is not an official Google product. At Google, they rely on many third party cryptographic software libraries. Unfortunately, in cryptography, subtle mistakes can have catastrophic consequences, and they found that […]
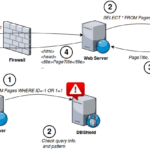
DBShield – Go Based Database Firewall
DBShield is a Database Firewall written in Go that has protection for MySQL/MariaDB, Oracle and PostgreSQL databases. It works in a proxy fashion inspecting traffic and dropping abnormal queries after a learning period to populate the internal database with regular queries. Learning mode lets any query pass but it records information about it (pattern, username, […]
Minion – Mozilla Security Testing Framework
Minion is a security testing framework built by Mozilla to bridge the gap between developers and security testers. To do so, it enables developers to scan with a wide variety of security tools, using a simple HTML-based interface. It consists of three umbrella projects: Minion Frontend, a Python, angular.js, and Bootstrap-based website that provides a […]