Anteater is a CI/CD Security Gate Check Framework to prevent the unwanted merging of nominated strings, filenames, binaries, deprecated functions, staging environment code/credentials etc. It’s main function is to block content based on regular expressions. Anything that can be specified with regular expression syntax, can be sniffed out by Anteater. You tell Anteater exactly what […]
Countermeasures
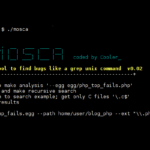
Mosca – Manual Static Analysis Tool To Find Bugs
Mosca is a manual static analysis tool written in C designed to find bugs in the code before it is compiled, much like a grep unix command. There are various ‘egg’ modules which contain patterns to scan for, it can scan through files recursively limited by file extension and logs results to an XML text […]
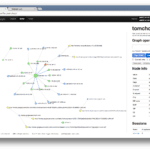
Malcom – Malware Communication Analyzer
Malcom is a Malware Communication Analyzer designed to analyze a system’s network communication using graphical representations of network traffic, and cross-reference them with known malware sources. This comes handy when analyzing how certain malware species try to communicate with the outside world. Malcom Malware Communication Analyzer Features Malcom can help you: Detect central command and […]
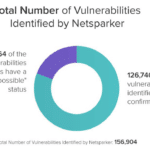
Web Security Stats Show XSS & Outdated Software Are Major Problems
Netsparker just published some anonymized Web Security Stats about the security vulnerabilities their online solution identified on their users’ web applications and web services during the last 3 years. Data-based stats like these, which are not based on surveys, can be pretty useful – at least to get a broad overview of what is going […]
How To Recover When Your Website Got Hacked
The array of easily available Hacking Tools out there now is astounding, combined with self-propagating malware, people often come to me when their website got hacked and they don’t know what to do, or even where to start. Acunetix has come out with a very useful post with a checklist of actions to take and […]