PowerShellArsenal is basically PowerShell for reverse engineering in a module format. The module can be used to disassemble managed and unmanaged code, perform .NET malware analysis, analyse/scrape memory, parse file formats and memory structures, obtain internal system information, etc.
PowerShellArsenal is comprised of the following tools:
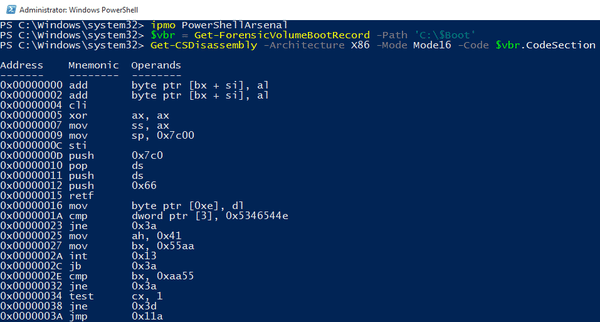
Disassembly – Disassemble native and managed code.
MalwareAnalysis – Useful tools when performing malware analysis.
MemoryTools – Inspect and analyze process memory.
Parsers – Parse file formats and in-memory structures.
WindowsInternals – Obtain and analyze low-level Windows OS information.
Misc – Miscellaneous helper functions.
Lib – Libraries required by some of the RE functions.
Usage
To install this module, drop the entire PowerShellArsenal folder into one of your module directories. The default PowerShell module paths are listed in the $Env:PSModulePath environment variable.
To use the module, type:
|
1 |
Import-Module PowerShellArsenal |
To see the commands imported, type:
|
1 |
Get-Command -Module PowerShellArsenal |
For help on each individual command, Get-Help is your friend.
You can download PowerShellArsenal here:
Or read more here.
