Oryon C Portable is a web browser designed to assist researchers in conducting Open Source Intelligence investigations. Oryon comes with dozens of pre-installed tools and a select set of links catalogued by category – including those that can be found in the OI Shared Resources. Based on SRWare Iron version 31.0.1700.0 (Chromium) More than 70 […]
Archives for 2014
Sony Digital Certs Being Used To Sign Malware
So at the end of November, Sony got owned, owned REAL bad – we wrote about it here: Sony Pictures Hacked – Employee Details & Movies Leaked. It seems in as a part of the massive haul of documents, the digital certificates used to sign software were also stolen. Which is bad, as you can […]
InsomniaShell – ASP.NET Reverse Shell Or Bind Shell
InsomniaShell is a tool for use during penetration tests, when you have ability to upload or create an arbitrary .aspx page. This .aspx page is an example of using native calls through pinvoke to provide either an ASP.NET reverse shell or a bind shell. ASP.NET is an open source server-side Web application framework designed for […]
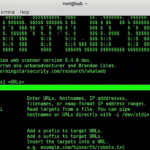
WhatWeb Download – Identify CMS, Blogging Platform, Stats Packages
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1500 plugins, each to recognise something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework […]
Sony Pictures Hacked – Employee Details & Movies Leaked
Sony hasn’t always had the best of times when it comes to being hacked, back in 2011 Sony basically had to rebuild the PlayStation Network (PSN) because of a hack which rendered the service off-line for almost a whole week. Plus the fact the PSN hack could have leaked up to 10 million user accounts […]