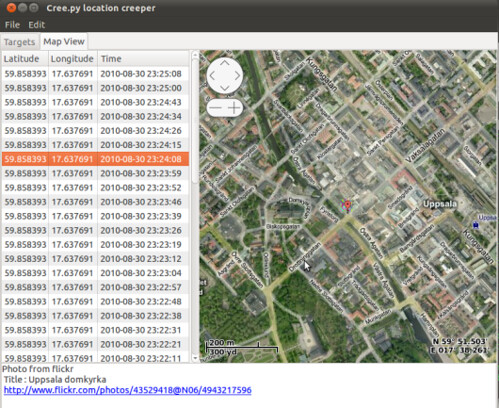
creepy is an application that allows you to gather geolocation related information about users from social networking platforms and image hosting services. The information is presented in a map inside the application where all the retrieved data is shown accompanied with relevant information (i.e. what was posted from that specific location) to provide context to the presentation.
Features
- Automatic caching of retrieved information in order to reduce API calls and the possibility of hiting limit rates.
- GUI with navigateable map for better overview of the accumulated information
- 4 Maps providers (including Google Maps) to use.
- Open locations in Google Maps in your browser
- Export retrieved locations list as kmz (for Google Earth) or csv files.
- Handling twitter authentication in an easy way using oAuth. User credentials are not shared with the application.
- User/target search for twitter and flickr.
Map Providers
- Google Maps
- Virtual Maps
- Open Street Maps
Information Retrieval Using
- Twitter’s tweet location
- Coordinates when tweet was posted from mobile device
- Place (geographical name) derived from users ip when posting on twitter’s web interface. Place gets translated into coordinates using geonames.com
- Bounding Box derived from users ip when posting on twitter’s web interface.The less accurate source , a corner of the bounding box is selected randomly.
- Geolocation information accessible through image hosting services API
- EXIF tags from the photos posted.
Social Networking Platforms Supported
- Foursquare (only checkins that are posted to twitter)
- Gowalla (only checkins that are posted to twitter)
Image Hosting Services Supported
- flickr – information retrieved from API
- twitpic.com – information retrieved from API and photo exif tags
- yfrog.com – information retrieved from photo exif tags
- img.ly – information retrieved from photo exif tags
- plixi.com – information retrieved from photo exif tags
- twitrpix.com – information retrieved from photo exif tags
- foleext.com – information retrieved from photo exif tags
- shozu.com – information retrieved from photo exif tags
- pickhur.com – information retrieved from photo exif tags
- moby.to – information retrieved from API and photo exif tags
- twitsnaps.com – information retrieved from photo exif tags
- twitgoo.com – information retrieved from photo exif tags
You can download creepy here:
Or read more here.
