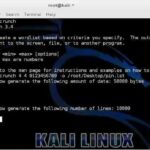
Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations. Some other options are: The Associative Word List Generator (AWLG) – Wordlists for Password Cracking CeWL – Custom Word List Generator Tool for Password Cracking RSMangler – Keyword […]
Archives for November 2010
TDL AKA Alureon Rootkit Now Infecting 64-Bit Windows 7 Platform
As we’ve come to expect, the malware guys are always at the leading edge of technological development. Now there are rootkits infecting 64-Bit versions of Windows, which have been thought of as fairly safe by most parties. The rootkit in questions is a fairly well known variant (TDL/Alureon) and has been around for several years, […]
Katana v2 (y0jimb0) – Portable Multi-Boot Security Suite
Katana is a portable multi-boot security suite which brings together many of today’s best security distributions and portable applications to run off a single Flash Drive. It includes distributions which focus on Pen-Testing, Auditing, Forensics, System Recovery, Network Analysis, and Malware Removal. Katana also comes with over 100 portable Windows applications; such as Wireshark, Metasploit, […]
PGP Users Locked Out With Latest OS X Update
For the past day or so I’ve been seeing endless people tweeting about how the latest Mac OS X update b0rks your Mac if you are using PGP full disc encryption. It’s a pretty nasty bug, but thankfully it can be recovered from fairly easily. If you are just looking for a quick solution, you […]
ddosim v0.2 – Application Layer DDOS Simulator
DDOSIM simulates several zombie hosts (having random IP addresses) which create full TCP connections to the target server. After completing the connection, DDOSIM starts the conversation with the listening application (e.g. HTTP server). Can be used only in a laboratory environment to test the capacity of the target server to handle application specific DDOS attacks. […]