[ad] Another teen hacker in the news, this guy looks like he has some formidable skills though with the list of crimes he’s perpetrated. He’s pleaded guilty though, so he should get a reduced sentence and he’s still classified as a juvenile offender being only 17 – so that works in his favour too. A […]
Archives for November 2008
Microsoft Security Assessment Tool – Free for Windows
[ad] The Microsoft Security Assessment Tool (MSAT) is a free tool designed to help organizations like yours assess weaknesses in your current IT security environment, reveal a prioritized list of issues, and help provide specific guidance to minimize those risks. MSAT is an easy, cost-effective way to begin strengthening the security of your computing environment […]
Spam ISP McColo Cut Off From the Internet
[ad] You might recall we reported a while ago about ‘spam friendly’ ISP Intercage coming back online after having their plug pulled by upstream provider UnitedLayer. They pledged to clean up their act though and drop their biggest client who was an Eastern European malware and phishing host. This time another ISP has been suspected […]
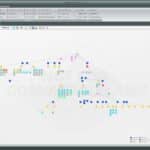
Maltego Download – Data Mining & Information Gathering Tool
Maltego download below, this open source intelligence and forensics application allows for the mining and gathering of information as well as the representation of this information in a meaningful way. The tool is used in online investigations for finding relationships between pieces of information from various sources located on the Internet. It uses the idea […]
Express Scripts Offers $1million Reward for Cyber Extortionists
[ad] This is an interesting story, I’ll be watching how it develops – it’s not often you see a bounty for online crimes and especially one as enticing as 1 million dollars! That’s a hell of a sum for nailing down some dodgy hackers who are running an extortion scam after a data leak. I […]