[ad] FireCAT (Firefox Catalog of Auditing exTension) is a mindmap collection of the most efficient and useful firefox extensions oriented application security auditing and assessment You can find an online map of Firecat v1.4 here. Changes for version 1.4 Information Gathering (Enumeration and Fingerprinting) Passive Recon : PassiveRecon allows Information Security professionals the ability to […]
Archives for November 2008
Spam Back on the Rise with Srizbi Resurrected
[ad] After McColo was partially disconnected from the Internet by it’s peers global spam dropped noticeably. It seems however that the spam was emanating from a zombie network and the control servers were hosted by McColo, the creators of the botnet (Srizbi) were smart about it though and built a fail-safe system into the the […]
Browser Rider – Web Browser Exploitation Framework
[ad] Browser Rider is a hacking framework to build payloads that exploit the browser. The project aims to provide a powerful, simple and flexible interface to any client side exploit. Browser Rider is not a new concept. Similar tools such as BeEF or Backframe exploited the same concept. However most of the other existing tools […]
Julie Amero Spyware Case Finally Comes To An End
[ad] It’s a sad case when someone loses their career over an incident which was outside of their control, not everyone can be expected to keep their computers free of spyware and malware. It just doesn’t happen. Unfortunately for Julie Amero, she got some porn pop-ups at the wrong time in a class full of […]
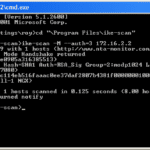
ike-scan – IPsec VPN Scanner & Testing Tool
ike-scan is a command-line IPSec VPN Scanner & Testing Tool for discovering, fingerprinting and testing IPsec VPN systems. It constructs and sends IKE Phase-1 packets to the specified hosts, and displays any responses that are received. IKE is the Internet Key Exchange protocol which is the key exchange and authentication mechanism used by IPsec. Just […]