[ad] It seems like ATM hacking is still the way to go for those into a bit of hardware hacking. One of the most notorious and well known ATM hackers was recently arrest in Turkey and a list of his tips discovered online where he also sold the ATM skimming equipment. Well his tips can’t […]
Archives for September 2008
dnsscan – DNS Open Recursive Resolver Scanner/Scanning Tool
[ad] Dnsscan is a tool for finger printing open recursive resolvers. It runs in conjuction with a small server that knows how to reply to queries forwarded from probed resolvers. For example, assume that you have delegated osd.example.org:
|
1 2 |
osd.example.org. 900 IN NS ns1.example.org. ns1.example.org. 900 IN A 10.0.0.1 |
On 10.0.0.1, you would run:
|
1 |
# ./dnsresponder -Q .osd.example.org |
On the client that initiates the DNS probes, you would […]
Brits Give Up Passwords For a £5 Gift Voucher
[ad] So it turns out you don’t need any fancy password cracking software like John the Ripper or Cain and Abel you just need a handful of £5 gift vouchers for Marks and Spencers! But we had discussed this in part before, some people will give out their passwords if you just ask, some if […]
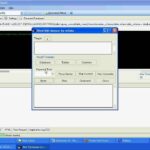
BSQL Hacker Download – Automated SQL Injection Tool
BSQL Hacker is an automated SQL Injection Tool designed to exploit SQL injection vulnerabilities in virtually any database. It aims for experienced users as well as beginners who want to automate SQL Injections (especially Blind SQL Injections). What Can BSQL Hacker Do? It ships with Automated Attack modules which allows the dumping of whole databases […]
Intercage – Spam/Malware Friendly ISP Back Online
[ad] There has been a big hoo-haa recently about a US ISP called Intercage who have said to have been harbouring spammers and scammers via their largest client an Eastern European webhost called Esthost. Their plug got pulled 2 days ago by the upstream provider IP transit provider UnitedLayer after weeks of criticism from the […]