MTR was written by Matt Kimball, with contributions by many people. Take a look at the “AUTHORS” file in the distribution. Roger Wolff took over maintenance of MTR in october 1998.
MTR combines the functionality of the ‘traceroute’ and ‘ping’ programs in a single network diagnostic tool.
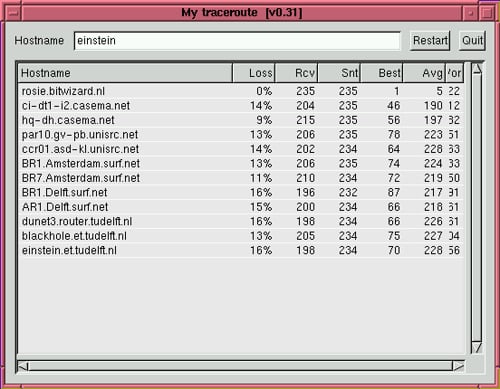
As MTR starts, it investigates the network connection between the host MTR runs on and a user-specified destination host. After it determines the address of each network hop between the machines, it sends a sequence ICMP ECHO requests to each one to determine the quality of the link to each machine. As it does this, it prints running statistics about each machine.
You can get MTR from the BitWizard FTP site at ftp://ftp.bitwizard.nl/mtr/.
You can find more info and binary packages at the MTR Site.

christian says
even better, and the REAL traceroute on steroids is LFT (layer four traceroute)
which can be found here
http://pwhois.org/lft/
Darknet says
Thanks christian, I shall look into that later.