WWWhack is a brute force utility that will try to crack web sites guarded by a web access password, here you can find the wwwhack hacking software free download. This utility can use a word file or try all possible combinations, and by trial-and-error, will attempt to find a combination of username/password that is accepted […]
Archives for December 2006
IE & Firefox Both Effected by Fake Login Flaw
[ad] It seems the recent fake login flaw effects both Internet Exploder and Firefox. Good to keep alert and with the new update mechanism it’s very simple to update your Firefox installation. The latest versions of both Firefox and Internet Explorer are vulnerable to an unpatched flaw that allows hackers to snaffle users’ login credentials […]
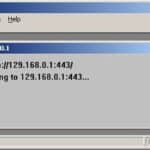
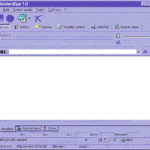
GoldenEye (GoldEye) Password Cracker – Download goldeye.zip or goldeneye.zip
GoldenEye is a brute-force password cracker hacking program and here you can download goldeye.zip or goldeneye.zip – it was written for web-masters to test the web application security of their own sites. This is an oldskool file, a lot of people are still looking for this. It should not be use by others to hack […]
Some Relaxing on the DMCA Regulations
[ad] There seems to be have been some slight relaxation on the DMCA regulations lately, which is a good thing for the majority of people! There have been many grey cases and sadly most have fallen on the side of the big corporations, finally something on our side! The U.S. Copyright Office specified new rules […]
TXDNS 2.0.0 Released – DNS Digger for Brute Force
[ad] TXDNS 2.0.0 has been released. TXDNS is a Win32 aggressive multithreaded DNS digger. Capable of placing, on the wire, thousands of DNS queries per minute. TXDNS main goal is to expose a domain namespace trough a number of techniques: Typos TLD rotation Dictionary attack Brute force This new version features a distributed model which […]